
Let’s dive into the world of iptables and learn how to write rules like a pro. It might seem daunting at first, but breaking it down step by step makes it much easier. We’ll tackle a practical example and see how the theory translates into real-world commands.
Understanding the Basics
Before we write any rules, it’s crucial to grasp the fundamentals. Iptables is a powerful firewall utility built into Linux. It works by inspecting network packets and deciding whether to allow, drop, or modify them based on a set of rules. These rules are organized into tables, the most common being filter (for general packet filtering), nat (for Network Address Translation), and mangle (for specialized packet alteration). Within each table, rules are further grouped into chains, like INPUT (for packets destined to the local machine), OUTPUT (for packets originating from the local machine), and FORWARD (for packets passing through the local machine).
Our Scenario: Blocking SSH Access from a Specific IP
Let’s say we want to block SSH access (port 22) from a specific IP address, say 192.168.1.100. This is a common task for securing your server. We’ll use the filter table and the INPUT chain for this.
Step 1: Accessing Iptables
First, we need to access iptables. We do this through the command line using the iptables command itself. You’ll likely need root privileges (using sudo) to make changes.
Step 2: Choosing the Right Table and Chain
As mentioned, we’ll use the filter table and the INPUT chain. We don’t need to specify the table explicitly since filter is the default.
Step 3: Writing the Rule
Now comes the core part: writing the rule. Here’s how we’d construct it:
sudo iptables -A INPUT -p tcp --dport 22 -s 192.168.1.100 -j DROP
Let’s break this down:
sudo iptables: Invokes the iptables command with root privileges.-A INPUT: Appends the rule to theINPUTchain.-Iwould insert it at a specific position.-p tcp: Specifies that the rule applies to TCP traffic (SSH uses TCP).--dport 22: Indicates that the destination port must be 22 (SSH).-s 192.168.1.100: Specifies the source IP address we want to block.-j DROP: This is the action.DROPsilently discards the packet.REJECTwould send an ICMP “connection refused” message.
Step 4: Saving the Rules
Crucially, iptables rules are not persistent across reboots by default. You need to save them. The method varies slightly depending on your distribution. On many systems, you can use:
sudo iptables-save > /etc/iptables/rules.v4 # For IPv4
sudo ip6tables-save > /etc/iptables/rules.v6 # For IPv6 (important!)
This saves the current ruleset. Your system should have a mechanism to load these rules at boot (often through a service like iptables-persistent).
Step 5: Verification
After applying the rule, test it! Try connecting to your server via SSH from the blocked IP (192.168.1.100). It should fail. You can also use iptables -L -v to list the rules and see the packet counters.
Important Considerations
- Order matters: Rules are processed sequentially. A more specific rule should come before a more general one.
- Default policy: If no rule matches, the default policy for the chain applies. You can set this with
-P. It’s often a good idea to have a defaultDROPpolicy and then selectively allow traffic. - IPv6: Don’t forget IPv6! Use
ip6tablesfor IPv6 rules, following the same principles. - Testing: Always test your rules thoroughly, ideally in a non-production environment first. A small mistake can lock you out of your server.
This example illustrates a basic but essential iptables operation. You can combine these building blocks with other options to create very sophisticated firewall rules. The key is to understand the flow of packets, the table and chain structure, and the various options available. Practice makes perfect!
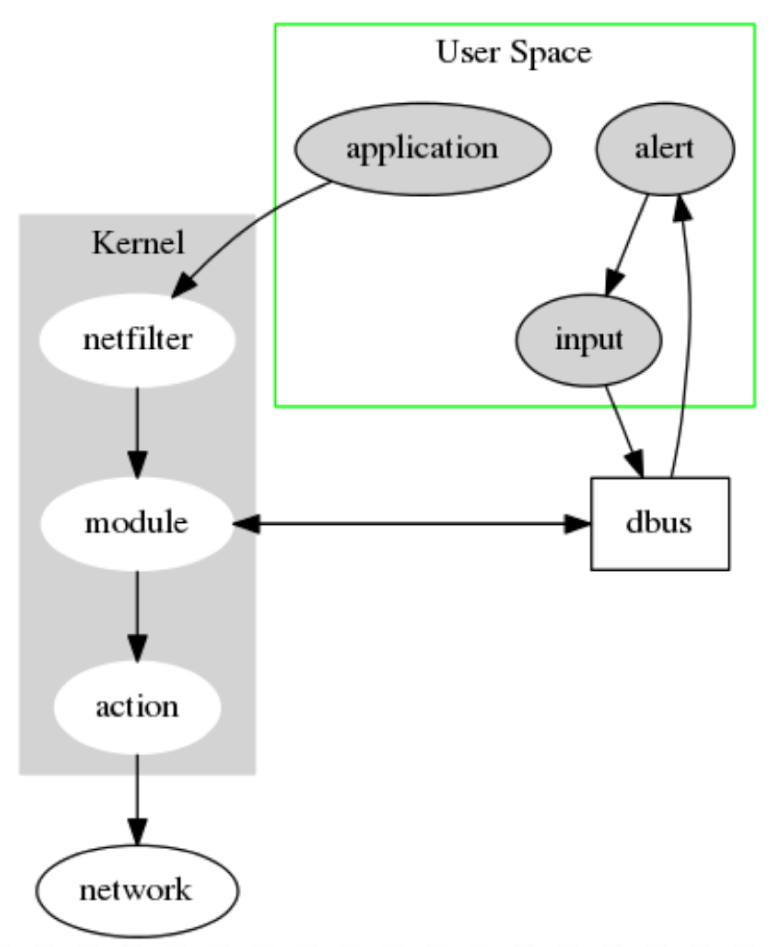
Iptables (execute Script, Log To Rdms/ Nosql, Dpi, Ngfirewall Etc.)
How To Write Iptables Rules For Ipv6

Adding/ Removing Rules In Iptables Ishy’s Blog

3 Ways To Make Iptables Persistent Dev Community

